Recent advances in quantum computing signal that efficient quantum computers may eventually come into existence. While many applications could benefit from this progress, this new computational paradigm can pose a threat to the security of communication technologies, and bring the downfall of part of current-use cryptography.
Among the cryptographic primitives whose security is threatened by quantum computing, public-key cryptography is arguably the most affected. The security of public-key cryptographic schemes (including RSA, RSA-PSS, ECDH, and ECDSA) relies upon the presumed hardness of particular mathematical problems, such as the RSA problem and the discrete logarithm problem. With only classical computers at hand, these problems are hard to solve. However, in 1994, Shor developed a quantum algorithm that can efficiently break them. In the event a powerful enough quantum computer is built, all common-use public-key cryptographic standards could be rendered vulnerable, harming the security of the wide array of applications of public-key cryptography, including encryption, digital signatures, digital cash, key agreement or time-stamping services. Hence, these applications should adopt cryptographic primitives that are secure against known quantum attacks, known as post-quantum primitives.
To the end of fostering a global transition to post-quantum cryptography, the National Institute of Standards and Technology (NIST) has launched its Post-Quantum Cryptography Standardization Process. This process is open and transparent, and it aims at selecting the next standard post-quantum cryptographic primitives. It started in 2016 with a total of 82 candidate cryptosystems, and it is now at the third round of evaluation, with just seven finalist candidates and eight additional candidates.
Once standards for post-quantum cryptographic primitives are selected, their adoption will entail intensive software and hardware implementation efforts in order to bring them to general use. Hardware implementations will require optimizing processors for these schemes, so that they run the selected candidates efficiently and securely. Among the existing platforms, the ones based in open-source and royalty-free architectures may inspire trust due to the transparency of their designs, on top of having a competitive legal and economic advantage in custom applications. This motivates the DRAC project to select RISC-V as the working architecture for the hardware development of NIST candidates.
"DRAC: Designing RISC-V-based Accelerators for next generation Computers" is a research project that started in June 2019, and which is led by the Barcelona Supercomputing Center-Centro Nacional de Supercomputación (BSC-CNS), in cooperation with the Polytechnic University of Catalonia (UPC), the University of Barcelona (UB), the Autonomous University of Barcelona (UAB), and the Rovira i Virgili University (URV). The project comes under the Research and Innovation Strategy for the Smart Specialisation of Catalonia (RIS3CAT) framework, and 50% of the budget comes from the European Regional Development Funds (ERDF) project.
The DRAC project strives to manufacture a processor and various application-oriented accelerators based on the RISC-V technology. The developed chips should be energy efficient, high performance, and suitable for supercomputing and large-scale computation use. A side-goal of DRAC is to foster the strategic technological sovereignty of Europe, since the whole continent is currently dependent on external infrastructures for chip design and manufacture, with the ensuing exposure to hardware vulnerabilities.
RISC-V offers many security advantages with respect to other ISAs. First, the transparency of the ISA makes designs auditable, with the complete view of chip designs not being restricted to the vendor. A second advantage is that the open-source nature of publicly available designs may help prevent hardware vulnerabilities, such as the recent Spectre and Meltdown bugs. Thirdly, the flexibility associated to the use of extensions allows to simplify chip designs, which can produce less vulnerable hardware and make the debugging process easier. And finally, its newness allows for a simpler and coherent instruction set, in contrast with other ISAs with legacy instruction issues, potentially reducing hardware vulnerabilities as a result.
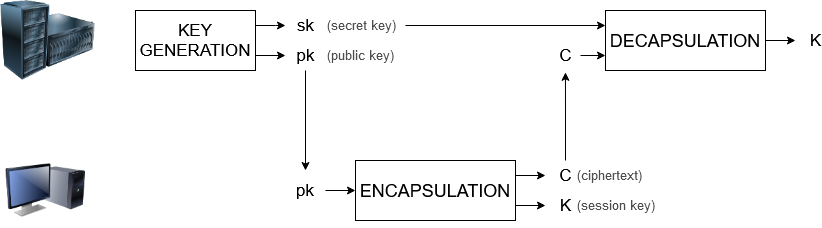
Driven by the concerns that quantum computing poses on currently employed public-key cryptography, and also by the advantages RISC-V offers with respect to other ISAs, the DRAC project targets the acceleration of post-quantum public-key cryptographic schemes. Out of the seven remaining final candidates of the NIST standardization process, three schemes have been selected to design secure accelerators and RISC-V extensions to incorporate into the RISC-V-based processor. We expect our hardware acceleration results to be deployed in RISC-V chips in two years.
Image: Digital signature protocol using the three algorithms that constitute a DS: Key Generation, Sign and Verify.
