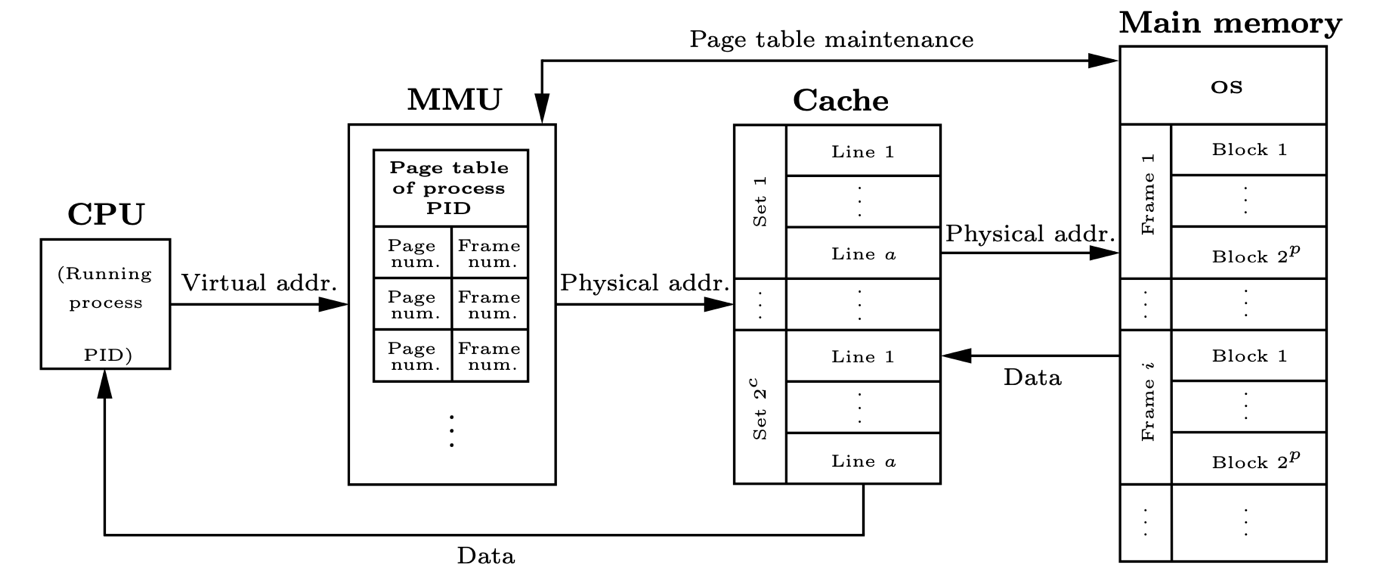
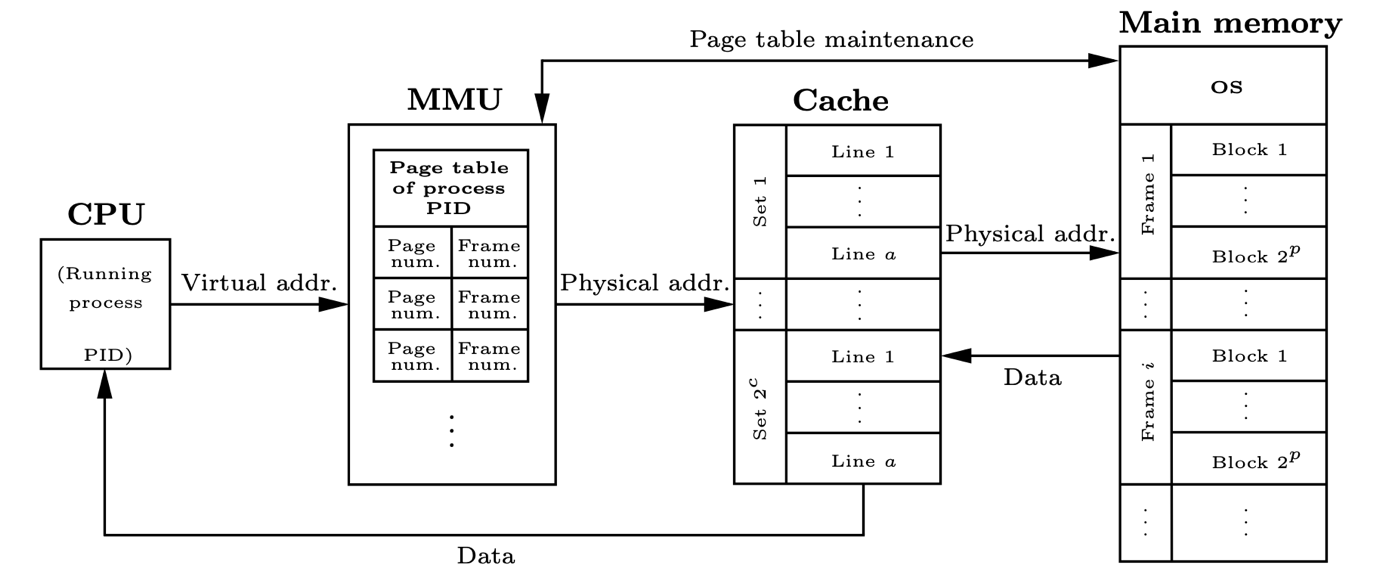
In computer architecture, caches are hardware storage components designed to mitigate the high latency issues of main memory accesses. The inherent low latency of cache accesses is vital for performance, and yet it can cause security problems. The access latency leaks to cores the information of whether or not data already resided in the cache hierarchy before the access took place. Cache side-channel attacks allow adversaries to learn sensitive information about co-running processes by using only access latency measures and cache contention. This vulnerability has been shown to lead to several microarchitectural attacks. A solution that aims at protecting against access-based attacks is cache randomization. Randomization-based protected caches (RPC) shuffle cache addresses so that accesses are distributed randomly in the cache. However, any RPC is expected to become insecure if attackers are allowed enough accesses.
One of the objectives of the DRAC project was to provide hardware solutions to this problem. First, we analyze the security properties of RPCs, and we provide a new notion of security that captures security against known attacks such as Prime+Probe and Evict+Probe. Then, using this definition, we obtain results that allow us to guarantee security by adequately choosing the rekeying period, the key generation algorithm and the cache randomizer, thus providing security proofs for RPCs under certain assumptions.
This work will be presented in the Conference on Cryptographic Hardware and Embedded Systems (CHES) 2022. The full version of the paper is available at https://eprint.iacr.org/2022/440.pdf
